Mission: ResMed, a world leader in medical software and connected health solutions, seeks to protect the security of information of our customers and their patients, our commercial partners, and our global team.
If you notice an issue with, or potential cybersecurity threat to, a ResMed-operated digital platform, please report it to us.
For further information regarding any of the topics below, please contact ResMed Web Security
ResMed strives to protect information in accordance with all applicable laws and regulations. In order to achieve a suitable level of cybersecurity, ResMed focuses on the following activities where appropriate:
On May 31st, 2019, ResMed plans to disable the use of TLS 1.0 across websites and services. This change will ensure we maintain secure communications with our partners, customers, and patients, and keeps us aligned with best practices in a changing cybersecurity landscape. ResMed will focus on supporting TLS 1.1 and 1.2.
TLS 1.0 is an older protocol and has weaknesses in its security which hackers have developed attacks against. Some attacks take advantage of outdated cryptography practices, while others utilize the more powerful computers today to break old cryptographic protocols that worked well against slower computers. Due to these reasons, ResMed will stop supporting TLS 1.0 as a protocol.
For the most part, this change will not affect you. Most modern internet browsers already use TLS 1.2, the current standard.
You can use one of the following website tools:
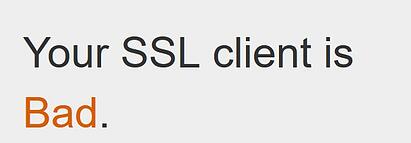
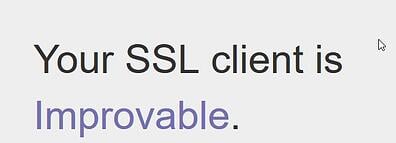
If the website shows your browser is “Bad,” then you will need to upgrade to a newer browser version. If you see “Probably Okay” or “Improvable” then you will still be able to access ResMed websites and services.
Example:
https://www.ssllabs.com/ssltest/viewMyClient.html
Under the Protocol Features section, if TLS 1.1 or 1.2 has a ‘Yes’ for supported then you will be able to connect successfully. It is not a problem if your browser also supports TLS 1.0.
Example:
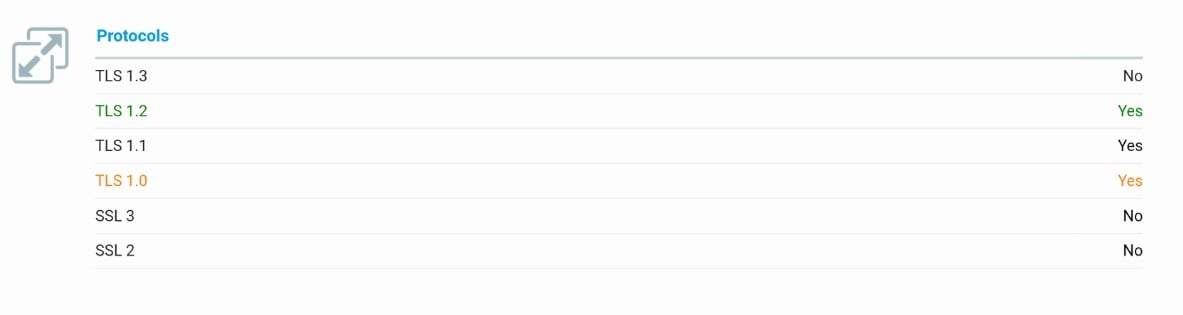
This section shows which browsers support more modern versions of TLS. While some older browsers will still work after TLS 1.0 is deprecated by ResMed, the most up-to-date version of a browser should be used to avoid other security vulnerabilities.
The following list is a compiled from various resources. Not all ResMed sites support the browsers below, but we list them to be complete.
| Name | Platform | Minimum Version | Recommended |
|---|---|---|---|
| Microsoft Internet Explorer | Desktop/Laptop | IE 8 (with Windows 7+) | 11 |
| Microsoft Edge | Desktop/Laptop | None | 18 |
| Mozilla Firefox | Desktop/Laptop | 27 | 65 |
| Google Chrome | Desktop/Laptop, mobile | 30 | 72 |
| Apple Safari | Desktop/Laptop | 7 | 12 |
| Opera | Desktop/Laptop, mobile | 17 | 58 |
| Samsung Internet | Mobile | 4 | 9 |
| Safari for iOS | Mobile | 5 | 12 |
| Microsoft Edge | Mobile | 1 | 1 |
If you connect to ResMed services through other technologies than a web browser, you will need to ensure that TLS 1.1 or TLS 1.2 are supported, which may require updating the environment your system is running in. We cannot provide an exhaustive list of options for these other technologies and programs, but you can test your system against ResMed websites and services today as TLS 1.1 and TLS 1.2 are supported already by our systems. If you do not check connectivity prior to the date mentioned above, your programs may not be able to connect to ResMed services.
Current APIs support TLS 1.1 and 1.2 if you need to test whether your system will function correctly after May 31st. If you have issues connecting to ResMed websites and services contact integration-support@resmed.com and the team can route you to the appropriate ResMed resource. Below are versions of common tools that support TLS 1.1 and 1.2.
| Version | TLS 1.1 | TLS 1.2 | Notes |
|---|---|---|---|
| 6 | Disabled | No | 1.1 available with update 111 |
| 7 | Disabled | Disabled | |
| 8 | Yes | Yes | Current version |
| Version | TLS 1.1 | TLS 1.2 | Notes |
|---|---|---|---|
| 3.5 and older | No | No | |
| 4.0 | No | No | Upgrade to 4.5 |
| 4.5-4.5.2 | Disabled | Disabled | Can enable by default in registry or in code |
| 4.6+ | Yes | Yes |
| Version | TLS 1.1 | TLS 1.2 | Notes |
|---|---|---|---|
| 1.0.0 and older | No | No | |
| 1.0.1+ | Yes | Yes |
Python compatibility varies depending on OS support for Python, documentation for this can be found on the official python site. Python 3.6 and 2.7.9 are compatible with TLS 1.2.
Computers use TLS (Transport Layer Security) to check each other’s identity and ensure they can talk privately. The technology allows you to communicate with ResMed while both protecting the communicated data and verifying the other side is trusted. The support for TLS, in various forms, has been added to many browsers and systems without intruding on a normal user’s experience. These security measures mean that passwords or credit card numbers can be sent over the internet without fear of someone else obtaining that information “in transit.”
In more detail, TLS checks certificates as a form of digital identification. Every TLS-enabled server would have a corresponding certificate that is automatically exchanged and verified during initial connection. A trusted party digitally “signs” the certificate verifying the system. Most operating systems and web browsers have a preconfigured list of trusted parties to compare. After checking the certificate, your web browser and the server will automatically decide how to protect the data using encryption.
For further information or any questions regarding TLS 1.0 deprecation, please contact ResMed Web Security